The use and growth of biometric facial software to confirm a person’s identity has sparked ongoing controversy regarding privacy laws and the right to consent. The terms adaptive facial recognition and biometric facial comparison are often used interchangeably, yet there are key differences between the two methods.
How Does Biometric Facial Software Work?
Both methods use machine-learning technology to analyze a face within an image. Biometric algorithms scan the image in search of common facial features including eyes, nose, mouth, and ears. Depending on the software complexity, the scan takes a deeper dive to analyze specific facial regions, including the nostrils, eyebrows, and iris. The data is then gathered and used to confirm a match.
Facial Comparison vs. Facial Recognition—What is the Difference?
Biometric facial comparison confirms identity using a one-to-one matching system. This means the software compares a real-time photo against an approved, stored image that the user has provided.1 In contrast, adaptive facial recognition uses a one-to-many matching system, comparing a real-time photo against large, third-party databases of stored records, and the user is unaware. The chart below further outlines the two methods, the key differences, and use case examples.
| Method | Biometric Facial Comparison (One-to-one matching process) | Adaptive Facial Recognition (One-to-many matching process) |
|---|---|---|
| Objective | Analyze, compare, and confirm | Analyze, calculate, predict, and confirm |
| Privacy | User aware | User unaware |
| Verification Method | Biometric photo matched against a previously enrolled image for the device | Biometric photos matched against a large database of photos |
| Use Case Examples | Mobile devices and applications for account access, password management, and login security Document verification to validate passports and driver’s licenses | Border patrol, airports, and cruise lines Criminal justice agencies including Federal Bureau of Investigation (FBI) and Department of Homeland Security (DHS) to aid forensic investigations, detect fraud, identify terrorists, and locate missing persons Social media platforms like Facebook, Instagram, and Snapchat to tag images |
Our Approach to Biometric Facial Technology
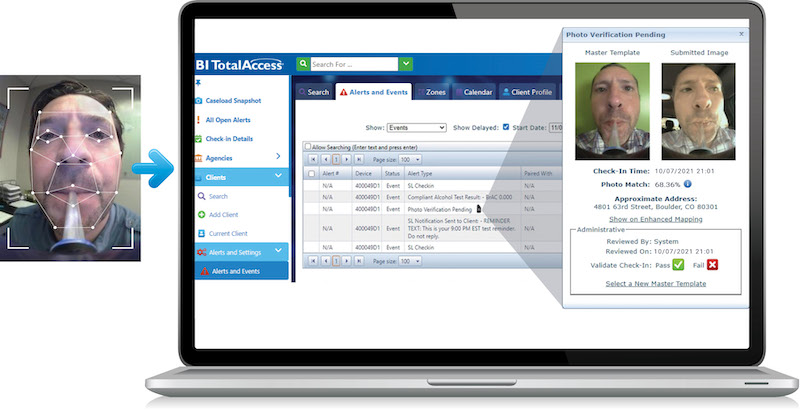
Community supervision has become increasingly mobile, and the methods to verify and confirm identity grows more complex. BI closely examines the use of all software before product implementation. Our mobile solutions including BI SmartLINK®, BI SL2®, and BI SL3® use the one-to-one matching process with user-provider images. The collected data/images provided by clients or officers are stored in BI TotalAccess®, and BI does not use mass facial recognition databases or share data with these third-party organizations. Our approach safeguards agency data and ensures individuals’ privacy, while reliably confirming the identity of the supervised client.